

By Tom Jacobson
Founder of Are We Safe Yet, Cybersecurity Analyst
We live in interesting times. Increased numbers of at-home workers means increased risk for your organization. Late last year my application for InfraGard was accepted by the FBI. As a member of InfraGard, a public-private consortium that seeks to keep the United States safe from cyber-attacks across a number of different industries, I get access to a steady stream of non-classified documents from the Federal government about cybersecurity and current threats.
The information below is what the FBI and other government agencies are recommending, so please take this seriously and pass this information on to anyone you think might benefit.
The FBI is reminding people to always use good cyber hygiene and security measures. By remembering the following tips, you can protect yourself and help stop criminal activity:
-
Do not open attachments or click links within emails from senders you don’t recognize.
-
Do not provide your username, password, date of birth, social security number, financial data, or other personal information in response to an email or robocall.
-
Always verify the web address of legitimate websites and manually type them into your browser.
-
Check for misspellings or wrong domains within a link (for example, an address that should end in “.gov” ends in “.com” instead).
Source link – https://www.ic3.gov/media/2020/200320.aspx
**Here is a PDF that contains some other information for CEOs about what they should be thinking about to protect their organizations and at-home workers.
Here is some information specific to COVID-related scams that are happening right now.
The FBI reports scammers are leveraging the COVID-19 pandemic to steal your money and your personal information, or both. Protect yourself and do your research before clicking on links purporting to provide information on the virus; donating to a charity online or through social media; contributing to a crowdfunding campaign; purchasing products online; or giving up your personal information to receive money or other benefits. The FBI advises you to be on the lookout for the following:
FAKE CDC EMAILS – Watch out for emails claiming to be from the Centers for Disease Control and Prevention (CDC) or other organizations claiming to offer information on the virus. Do not click links or open attachments you do not recognize. Fraudsters can use links in emails to deliver malware to your computer to steal personal information or to lock your computer and demand payment. Be wary of websites and apps claiming to track COVID-19 cases worldwide. Criminals are using malicious websites to infect and lock devices until payment is received.
PHISHING EMAILS – essentially a more sophisticated version of spam, these automated emails may pose as contacts you know and ask you to do specific tasks that involve purchases. Look out for phishing emails asking you to buy gift cards or ask you to verify your personal information to receive an economic stimulus check from the government. While talk of economic stimulus checks has been in the news cycle, government agencies are not sending unsolicited emails seeking your private information to send you money. Phishing emails may also claim to be related to charitable contributions, general financial relief, airline carrier refunds, fake cures and vaccines, and fake testing kits.
Some tips for employers and employees re phishing emails posing as a colleague:
-
Explain that employees will never be asked to perform “a quick task” through email – that phrase is a red flag and is used by a lot of these phishing emails.
-
Set a policy that employees will never be asked to perform money-related tasks through email – a phone call is mandatory for anything involving money!
-
If any money-related requests come through, employees must forward the email and call colleague on the phone to verify immediately.
-
Employees are not allowed to process/handle any kind of money requests on their smartphones – only on their laptops or PCs, and never after 5:00 pm at night.
(That last point might sound strange, but it’s important. I’ve noticed that people are a lot more trusting of information that comes through on their phones, and red flags that they would normally catch on their laptops or work computers get missed or ignored. I think one reason is that everything is so small on the phones that bogus email addresses just don’t get seen in the same way. Also, people are much “twitchier” on their phones and act without thinking to click links. Not a good combination! )
COUNTERFEIT TREATMENTS OR EQUIPMENT – Be cautious of anyone selling products that claim to prevent, treat, diagnose, or cure COVID-19. Be alert to counterfeit products such as sanitizing products and Personal Protective Equipment (PPE), including N95 respirator masks, goggles, full face shields, protective gowns, and gloves. More information on unapproved or counterfeit PPE can be found at www.cdc.gov/niosh. You can also find information on the U.S. Food and Drug Administration website, www.fda.gov and the Environmental Protection Agency website, www.epa.gov. Report counterfeit products at www.ic3.gov and to the National Intellectual Property Rights Coordination website at iprcenter.gov
Finally, here’s one scam that two of my clients here in Mendocino County have received in various forms. This is a very sophisticated phishing email designed to access an organization’s email, and by extension, every online account they have access to (including bank accounts). It is without a doubt the scariest thing that I have seen online, and familiarizing yourself with it may prevent a data breach or worse for your organization.
It starts out with a very legitimate-looking email like this one:
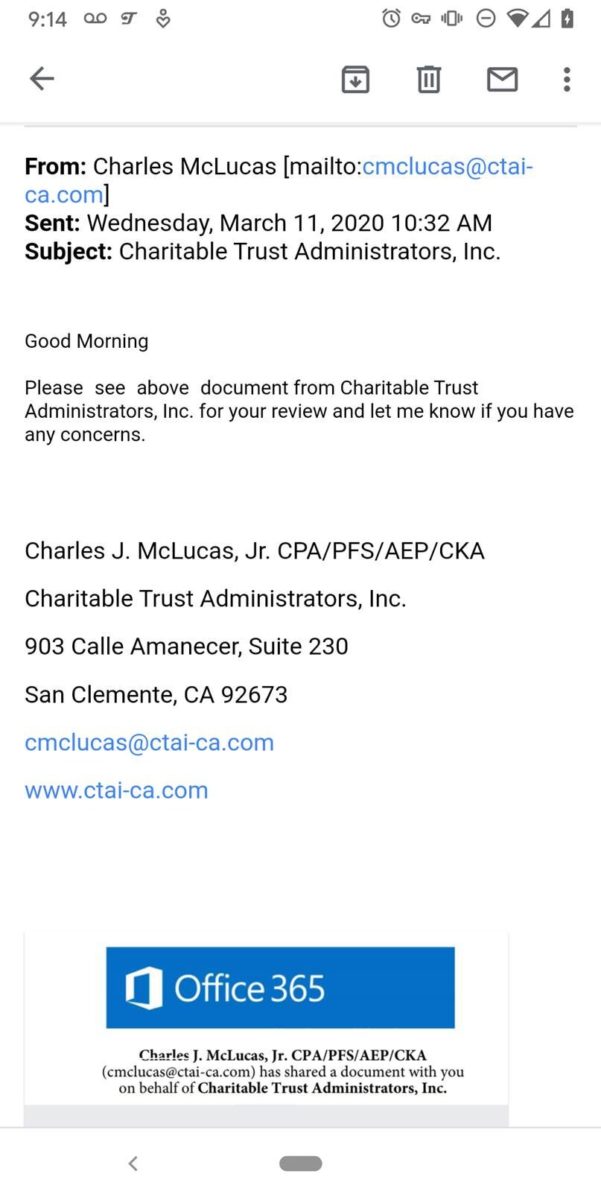
In both cases, the email was from someone that the intended victim either knew or had already had some contact with, making it even more trustworthy. Because the email account it came from had been hacked (in this case, the email of Charles J. McLucas, Jr.) it was actually sent from his real email, making it even more believable. As a side note, I actually called Mr. McLucas and he explained that yes, his email had been hacked, and I was the 700th person who had called him that day! His email account was undoubtedly compromised through a similar phishing email.
The attachment pictured at the bottom of the email is a PDF. Opening the PDF brings the victim here:
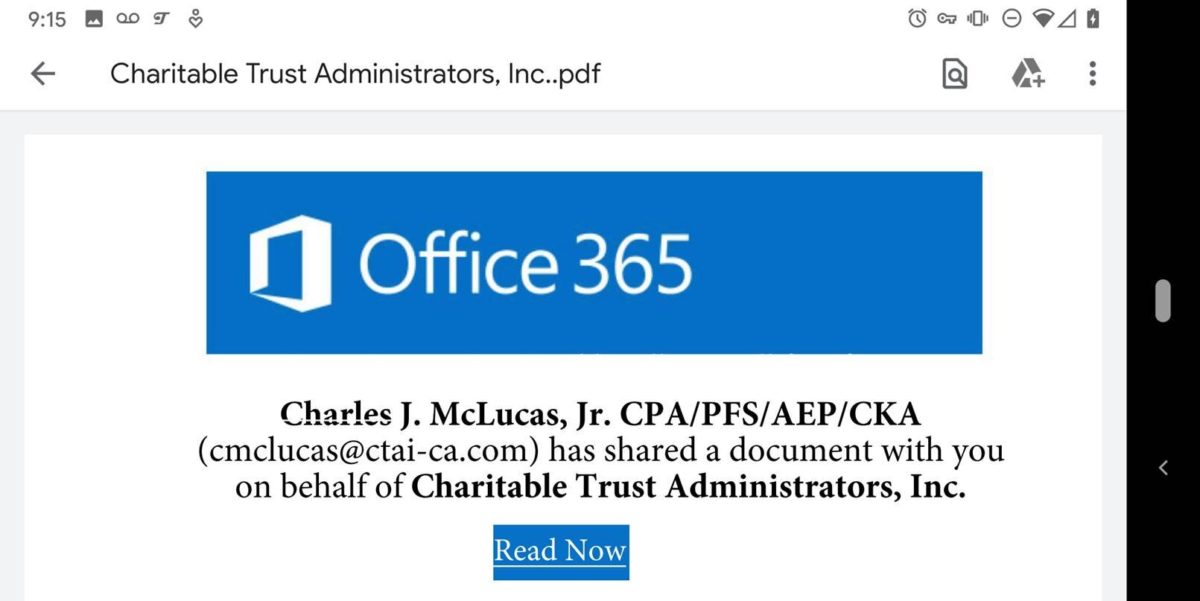
The PDF seems pretty harmless, with only a link to a supposed document for your inspection. Clicking the link takes you here:
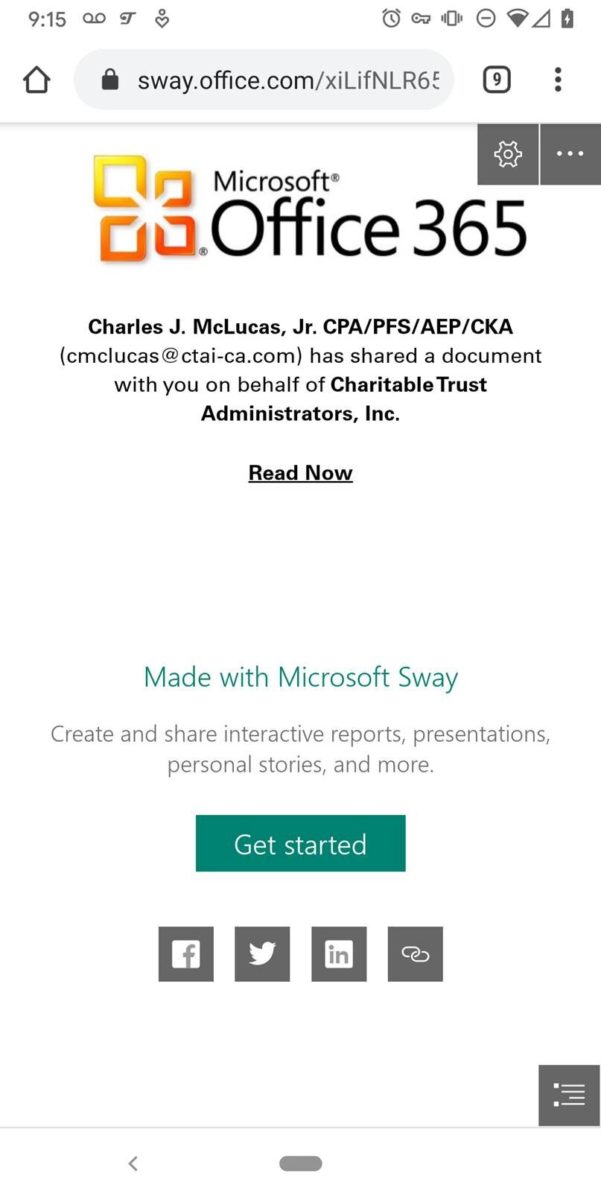
What’s really confusing about this is that it is an actual Microsoft website, albeit one for a product most people have never heard of (Sway, a PowerPoint-like system). This is also legitimate in the sense that it really is a page hosted by Microsoft. At this point the victim is thinking, come on already! – and is probably so eager to get to the “actual” file that they are unprepared for what comes next:
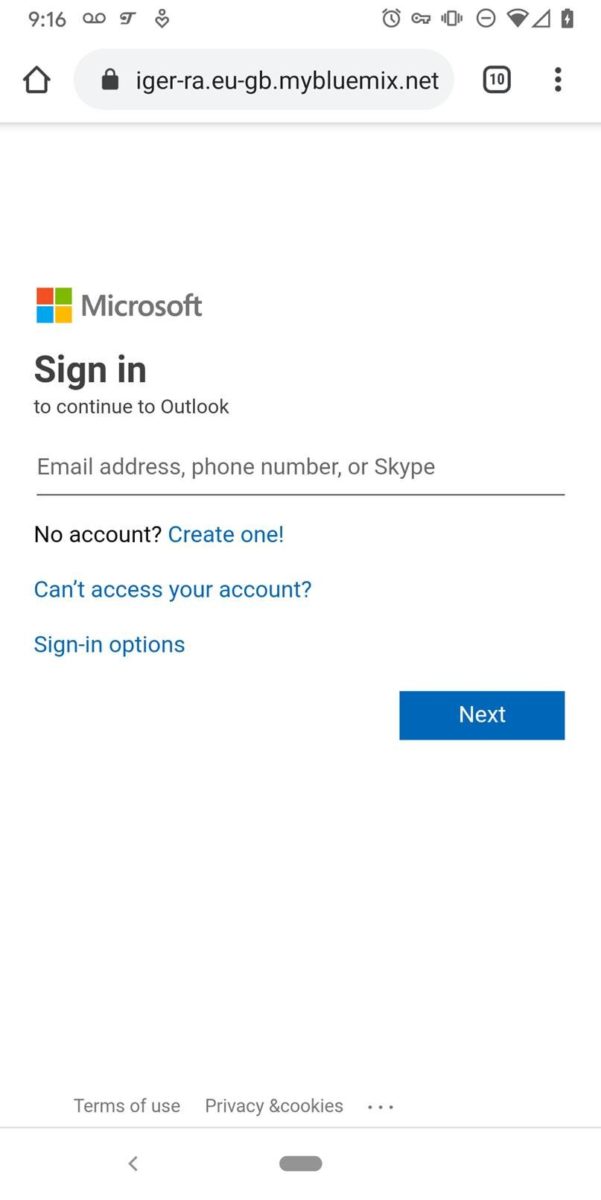
This is the beginning of the end – a very realistic-looking sign-in page for Office 365 – that is not hosted by Microsoft! You can see part of the URL in the screenshot (mybluemix.net is the end of the domain) but by this point, most victims are beyond suspecting anything and just fill in their username and password. This system is sophisticated enough to check the entered username and password in real-time, and then determine if any two-factor authentication is in place. If it is, it asks for the 6-digit 2FA code – at which point your organization has officially experienced a data breach. I’m pretty sure this is what happened to the local hospital (my wife received a data breach notice from them last month) so please take this seriously – in principle, this is exactly the same technique that Russian government actors used to gain access to the DNC’s email in the last election!
Please note that although this example uses Office 365, there is an identical phishing scam for GSuite / Gmail.
If you see anything even remotely resembling what is described above – please do not click on it (or stop clicking if you have already started).
How to do Business in the Age of Corona Virus
As the number of California cases of COVID-19 rises, the team at West Business Development Center wants you to know we are here to help. Stay informed and learn more about the resources available on our Corona Virus Resource Page Here.
Of course, there are many educational activities that you can engage in during this time. West Business Development Center is providing ongoing educational webinars on a variety of topics. Visit this page on West Center’s website for more information or contact us here to work with a business adviser.

